Understanding IP Address Abuse: Types, Detection & Prevention Methods

Wondering what is IP address abuse?
Every networking device, from phones to servers, uses an IP address to link up and swap data across the internet, anchoring network communication.
Yet, this setup is a magnet for IP address abuse, with abusers twisting addresses for malicious attacks like spam, phishing, or spoofing. IP abuse impacts network security and can throw business operations into chaos, while exposing sensitive information. That’s why it’s extremely critical for organizations to prevent these threats.
At ServerMania, we empower clients with Dedicated Hosting, Cloud Hosting, and IP Transit, which offers robust safety solutions to mitigate risks. Our tools streamline IP management for safer networks, ensuring reliable connectivity and protection against threats.
In this quick guide, we’ll go over common types of IP abuse, detection, and prevention to protect your network and keep traffic flowing from legitimate sources.
Introduction to IP Addresses
An IP address is in the core of internet communication, acting as a unique identifier for any devices like smartphones, laptops, or servers that are connected network. It provides data exchange that enables everything from web browsing to online video streaming but leaves the door open for IP address abuse.
IP addresses are vital to business operations, and their misuse can leak sensitive information or swamp services with malicious traffic. Hence, understanding their function and the risks of abuse helps many organizations and users to locate and prevent abuse incidents, keeping networks safe from disruption.
Tip: If you’re interested in learning more about how addresses work, check our IPv4 vs IPv6 guide!
What Is IP Address Abuse
When an IP address is used with harmful intent, it becomes IP address abuse, turning a connection tool into a weapon for attacks on the internet.
This type of abuse threatens networks and users, and requires immediate response from organizations to protect network safety and maintain operational integrity.
Common IP abuse examples include phishing attacks, spam, or IP spoofing, where attackers disguise their IP to unleash malicious flow or grab sensitive information. This misuse can impact many services, deceive readers into leaking data, or destabilize networks.
So, by acquiring skills to investigate and counter threats, businesses can safeguard resources, maintain legitimate source traffic, and promote a more secure internet.
What Is IP Abuse: The malicious use of an IP address to conduct harmful activities, such as phishing, spam, IP spoofing, IP hijacking, or IP address scanning), which compromises network safety, disrupts services, steals sensitive data, or deceives users by exploiting traffic or open ports.
Common Types of Address Abuse
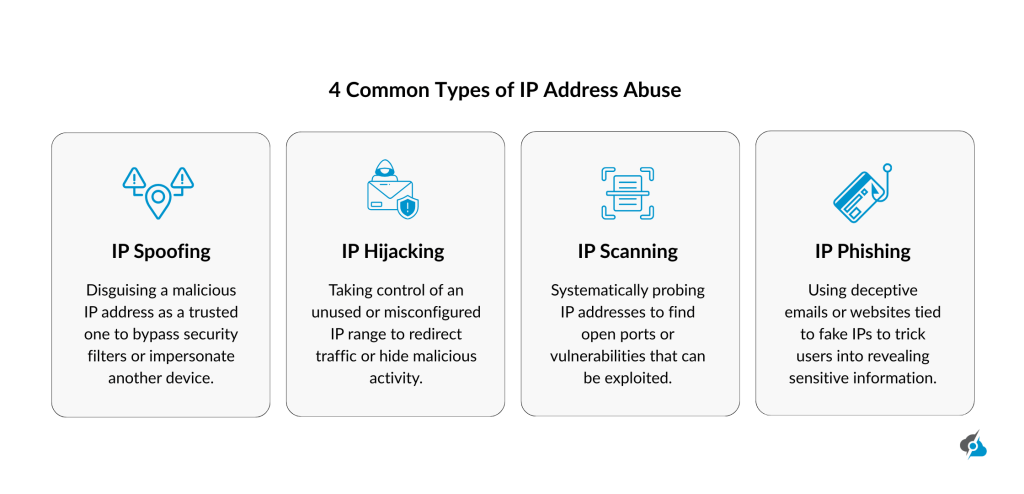
IP address abuse takes many shapes, each posing unique threats to the network safety and business operations. Below, we will outline the 4 most common cases of abuse, detailing how attackers exploit IP addresses to disrupt services, steal data, or deceive readers.
IP Spoofing
Attackers use IP spoofing to fake the IP address in packet headers, posing as a legitimate source to launch attacks like man-in-the-middle or denial-of-service. This malicious activity hides the abuser’s true location, making it tough to trace or prevent the malicious intent.
This can ultimately jam networks or manipulate sensitive data exchanges!
IP Hijacking
In IP hijacking, or prefix hijacking, the attackers wrongly claim IP address blocks owned by others, that redirects the traffic to steal data or disrupt services. This abuse decreases trust in routing tables and can cripple network integrity, leaving organizations struggling to restore admission for users.
IP Scanning
Through IP address scanning, attackers probe IP addresses to find open ports and active devices, hunting for weak spots to exploit with harmful software or unauthorized entry. This investigation fuels intrusion by mapping network vulnerabilities, putting resources and crucial information at threat.
IP Phishing
In phishing, spoofed IP addresses let cybercriminals send messages that look like they’re from trusted operations, tricking users into sharing data or clicking malicious links. This form of abuse drives spam and malware spread, leading to breaches that impact business operations.
| Comparison of IP Abuse Types | |||
|---|---|---|---|
| Method: | Impact: | Detection: | |
| Spoofing | Fakes the IP address to the mask exploiters | Disrupts operation, and steals data | Monitor traffic for odd requests |
| Hijacking | Steals IP blocks to reroute traffic | Breaks network integrity | Check routing tables for anomalies |
| Scanning | Probes open ports for weaknesses | Enables malware breaches | Use intrusion detection for activity |
| Phishing | Spoofs IP for repetitive messages | Tricks users into leaking information | Filter malicious email traffic |
The Impact When IP Abuse Occurs:
IP address abuse can turn networks upside down, impacting the network safety where it matters the most. When exploiters sneak IP breach through IP hijacking they can steal sensitive data, causing breaches that wreck the entire organization privacy.
Harmful traffic from denial-of-service attacks might knock operations offline, leaving users stranded and business operations in chaos.
Also, if exploiters mess with the data, feeding fake messages into computers, it throws off the integrity and trust in the system. These incidents drain the organizations’ wallets and reputations, so it’s vital to respond quickly and mitigate threats.
IP Abuse Detection
Identifying address abuse is the first step to keeping businesses’ networks safe from the malicious threats and attackers. All businesses should monitor the traffic for odd patterns, like spikes in requests or unusual connection attempts, which could signal attacks such as address spoofing or phishing.
Tools like intrusion detection systems identify abusive addresses by flagging harmful traffic, while logs help investigate activity tied to spam.
Hence, regular reviews of network files can catch exploiters early, protecting critical information!
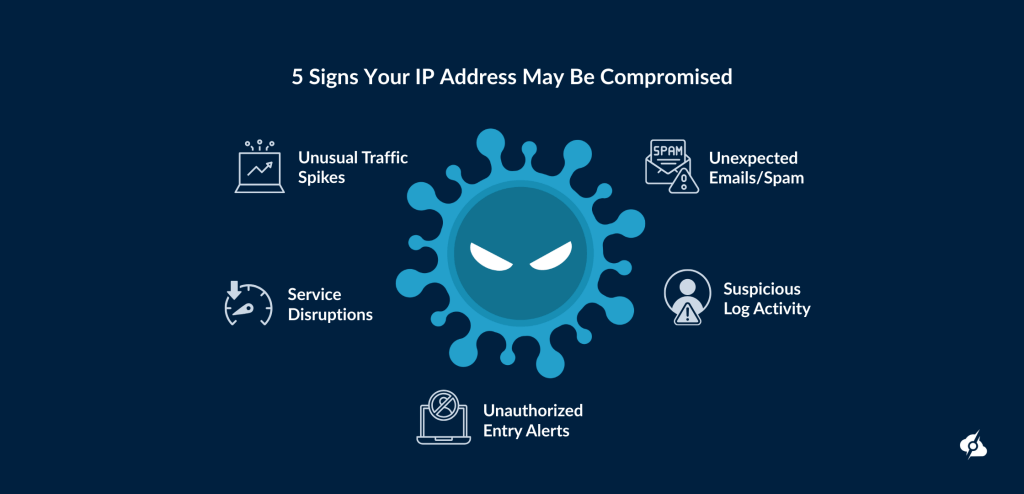
Signs Your IP May Be Compromised
Here are some signs that your IP may be compromised:
- ❌Unusual Traffic Spikes: Sudden surges in traffic to your servers, hinting at harmful traffic like DDoS attacks.
- ❌ Suspicious Log Activity: Logs show odd connection attempts or free ports being probed, suggesting address scanning.
- ❌Unexpected Emails/Spam: Users report spam or phishing tied to your IP, indicating address spoofing.
- ❌Service Disruptions: Services slow or crash due to malicious behavior, potentially from IP hijacking.
- ❌Unauthorized Entry Alerts: Alerts of entry attempts to sensitive data or resources, pointing to abuse.
Note: If you spot these signs, report the issue to your network admin immediately.
Common Forms of Network Security
Safeguarding networks from address abuse is a must.
From flooding inboxes to IP spoofing masking malicious traffic, the threats are real and can cripple business operations. By deploying smart security measures, organizations can protect their networks, safeguard important information, and keep operations running smoothly.
Let’s next review the 10 practical IP abuse prevention tips, each designed to prevent breaches and maintain network protection.
1. Lock Down Control Access
Keeping unauthorized entry is the most important factor, since exploiters tend to sneak into networks through the weakest spots.
Organizations can shut the door closed by using multi-factor authentication (MFA) to double-check visitors and role-based access control (RBAC) to limit who gets in based on their job. Hence, regularly checking and updating these safety policies keeps networks tough to crack, reducing risks of incidents.
2. Check the Network Activity
Another important factor is watching network traffic, that helps catch an exploit before things escalate. Tools like intrusion detection and prevention systems (IDPS) can easily spot odd activity, while real-time IP abuse monitoring flags weird patterns.
Any detailed logs can track visitors and traffic, and Security Information and Event Management (SIEM) tools dig into potential threats. This investigation setup is crucial for locating malicious strikes early.
3. Harden Your Network Setup
A rock-solid network foundation can catch exploiters red-handed. Firewalls, especially next-generation ones, block harmful traffic, while splitting networks into segments shields sensitive data. Encryption like TLS or VPNs keeps the data safe, and routine patches on routers and computers patch any openings that attackers might exploit.
4. Authentication & Passwords
Weak passwords are an open invitation for attackers. Requiring strong, complex passwords, refreshed often, alongside security tools like password managers, shuts down easy entries. An account lockout rules stop brute-force breaches in their tracks, so it’s crucial to boost the front line protection as much as possible.
These steps mitigate intrusions by making networks tougher to breach!
5. Identify & Stop DDoS Attacks
Distributed denial-of-service (DDoS) attacks can impact services and hit business operations harshly, which is a major threat. Businesses can fight back with DDoS mitigation services to soak up bad traffic, rate limiting to control requests, and content delivery networks (CDNs) to spread the load.
These protection tactics keep networks online.
6. Prevent Malware & Phishing
The malware and phishing attempts trick users into providing critical information. Email filters and anti-phishing tools block shady emails while endpoint detection and response (EDR) watches for threats. Hence, regular security training helps employees spot malicious activity, reducing the room for breach.
Note: A phishing intrusion can be masked such as a simple company email, prompting the reader to click the link, opening the door to ultimate vulnerability.
7. Apply Patches and Updates
Old software is a safety gap that attackers can easily breach. So, keeping computers, apps, and systems updated with the latest patches, ideally through automated tools, closes vulnerabilities fast.
This crucial habit mitigates threats by keeping networks secure from breaches.
8. Secure the Remote Access
Remote admission can be a network’s weak link if not locked down. Secure VPNs and Zero Trust Network Access (ZTNA) verify every connection, while monitoring third-party entries and using network access control (NAC) ensures device safety.
9. Build a Strong Response Plan
Even with the top protection, abuse cases can slip through. Hence, a solid action plan, tested often, with automated safety triggers and backup resources limits damage. This preparation reduces the responding delay, mitigates attacks and keeps business operations steady.
10. Train Personnel to Spot Threats
Employees are often the weakest security link, but training changes that. So, regular security awareness sessions teach clients to report malicious behavior and follow network protection rules. Clear policies on network use mitigate intrusions by empowering employees.
Now that we know some tips on how to prevent IP abuse, let’s next answer some of the most frequently asked questions!
Frequently Asked Questions
What is IP address abuse?
IP address exploitation occurs when exploiters misuse an address for malicious attacks like, phishing or spoofing, harming networks.
When did address abuse become a major issue?
IP address abuse surged in the 2000s as internet use grew, with attacks like malware and spoofing targeting business operations.
How can businesses detect IP exploitation?
Organizations can identify abuse by monitoring traffic for malicious activity, using logs and intrusion detection to spot abusive IP addresses.
How can businesses prevent IP abuse?
Businesses mitigate abuse with firewalls, safety training, and Network Address Translation to block malicious traffic and secure networks.
Why is reporting IP abuse important?
Reporting abuse incidents to IPXO Marketplace or admins helps investigate exploiters, stop attacks, and protect network integrity.
How to report IP abuse?
To report IP address misuse, log the attacker’s address, traffic details, and specific case, then submit a report to your network admin.
Can IP abuse impact customers?
Yes, abuse like phishing can trick customers into sharing information, disrupting services and eroding trust in businesses.
Protect Your Network, Power Your Growth
IP abuse can quietly erode trust in your business, causing issues like blacklisted domains, service disruptions, and damaged deliverability. While some of these threats stem from bad actors, others happen when systems aren’t properly monitored or secured. Knowing how to spot the signs and take preventative action can save you major headaches down the line.
At ServerMania, we don’t just provide infrastructure, we partner with businesses to help them build stronger and safer networks. With our proactive abuse prevention measures, 24/7 support, and soon-to-launch IPv4 leasing service, you’ll have access to clean, well-managed IP addresses ready for your next project.
Ready to scale with confidence? Explore ServerMania’s secure hosting solutions and stay tuned for our upcoming IP leasing launch.
Was this page helpful?

